Power BI
Submitted by darnold on Fri, 04/26/2024 - 13:17Power BI Reporting - Early Access
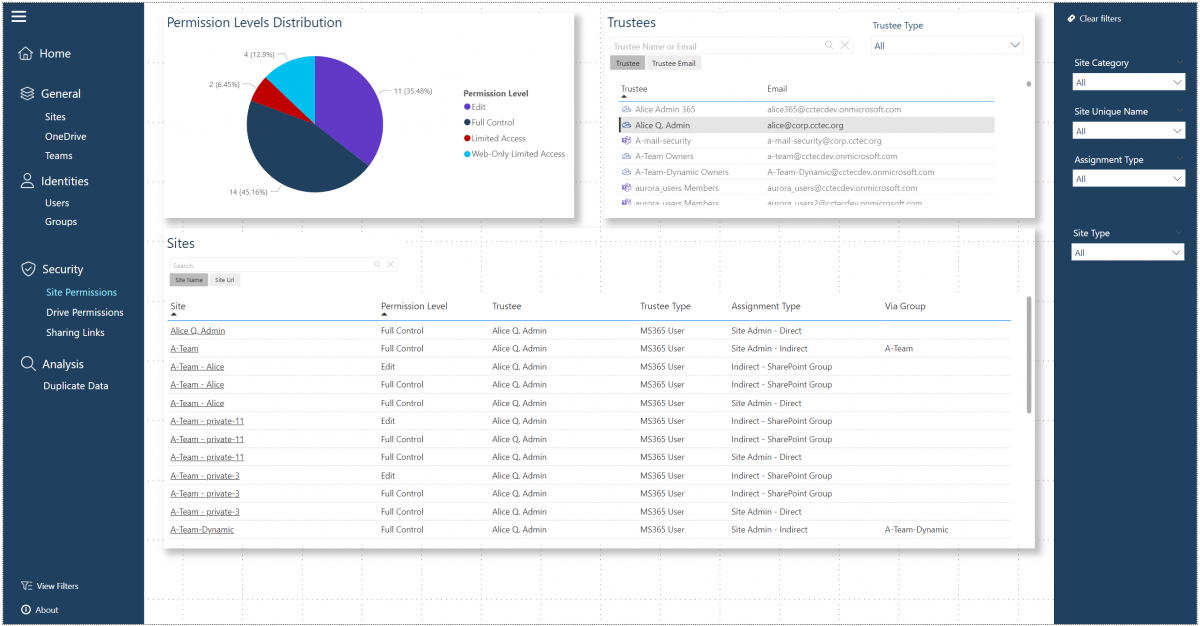
Starting with the 24.2 release of Galileo and File Reporter, we have introduced Early Access integration support for Power BI reporting.
This site provides SQL queries and report templates for use with the Galileo and File Reporter file system analysis products.
See the How-To Guides for instructions on how to import and use the provided queries and reports from the Recipes page.

Starting with the 24.2 release of Galileo and File Reporter, we have introduced Early Access integration support for Power BI reporting.
New with version 4.0 is ability to scan and report on permissions and sharing within Microsoft 365. Know how the permissions are set and how files are sharing can make a large impact on how well a company’s data is protected.
This report comes in a couple of formats. First a custom paginated format and secondly a CSV based format.
NOTE: Due to schema changes in 4.1, be sure to download the appropriate version for your installation.
A customer needed to create a report for management that shows the file and folder counts, the users quota, and how much of their quota was being used. This customer wanted all empty directories to be ignored.
This custom query shows a summary of the folders in the path provided on line 7. The report summaries the file and folder counts, size used, the quota value set, and the quota remaining.
Note: This query is written for Active Directory and can be modified for use with eDirectory.
This is file extension report that displays the fullpath, filename, size, owner, scan_target, and file_extension from the srs.current_fs_scandata database view, and is limited to current scan data.
Although, this query is written to report on media based file extensions, line 16, can be modified to any set of file extensions needed.
Copyright © 2026, Condrey Corporation
